OK cool, so Module 5 is able to alert about services and drivers that are loaded by processes.
No, I haven’t been able to test SS 15 yet, because it won’t run on my Win 10 machine. But I’m trying to figure out how SS 15 compares to SS 12 which I’m still using. What I basically understand is that you guys developed SS 15 from scratch and it isn’t using any code of SS 12, correct?
And because of certain changes in Win 11, you haven’t developed certain features yet. I get that, but stuff like smarter process control (LOLBins), a firewall, anti-code injection and possibly keystroke encryption should still be possible to add. I say this based on what I see with other security tools which supposedly run just fine on Win 11.
I will try to explain. Let’s say that I ask for a feature like anti-code injection, and your reply to me is, that I shouldn’t worry about it, because SS will make sure that malware doesn’t run at all. But isn’t this the job of an AV like Windows Defender?
To give some background info, I have been using SpyShelter for 15 years or so, and I have always disabled the anti-executable feature, because it’s annoying to me. Why alert me every single time when a process/app tries to launch? If a user downloads and runs/installs some app and the AV says the file is clean, then why should SS alert me about it?
In other words, I see this feature (that some may actually like) as pointless, I’m more interested in monitoring app behavior when apps already run in memory. That’s the reason why I have been using SS for all of these years. So I’m disappointed to see that SS 15 is missing a couple of crucial ‘‘app behavior monitoring’’ features.
And it’s not so much that I believe that SS is acting like an AV, but isn’t it true that SS might block some apps from running when identified as being malware? So that’s why I asked if you guys were using a third party AV engine or the cloudbased VirusTotal service? ![]()
Thanks again for your feedback and interesting discussions! It’s cool you used SpyShelter Classic for so long! For me it’s super fun and refreshing to have someone come in and discuss all our features and how we can improve!
About your comment above, I still wonder if you haven’t tried our latest version? I ask because our Application Control feature doesn’t work like you say “alert me every single time when a process/app tries to launch”. I agree that would be SUPER ANNOYING! Perhaps our old Classic version worked that way?
Please let me explain how Application Control works with our latest software.
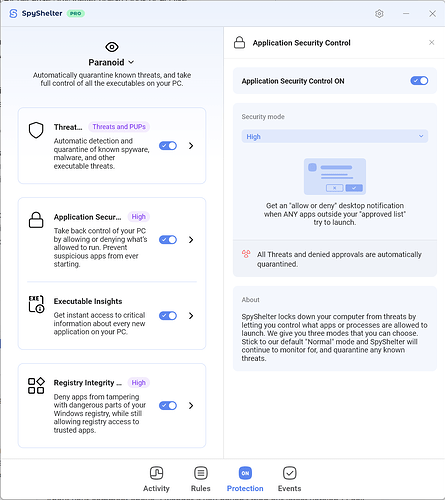
Please see the Application Control feature above from my own SpyShelter. You’ll see I choose “High” mode, so if a new .exe with an unknown publisher, or an unsigned executable tries to launch SpyShelter will stop it. But, I can choose to allow it if I want with our allow/deny window.
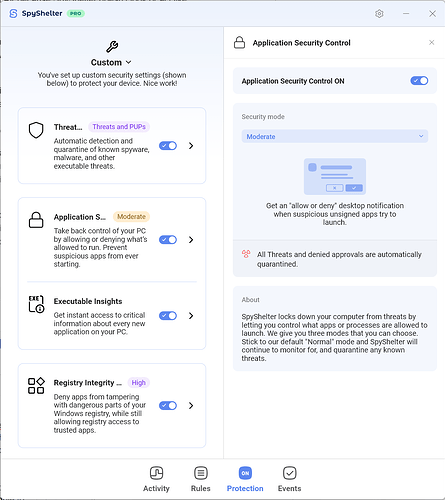
It sounds like you find that feature annoying though, so you could switch to our “Moderate” setting, where only unsigned executables will be held and unable to launch. Please see below the top right description.
But, do you even hate blocking unsigned executables because you work with them often, or maybe you’re a software developer that does? No problem, switch to Normal mode and you won’t get these at all. You can also switch off the feature completely on the left side (see the big switch?).
I’ll explain how I and a lot of SpyShelter users use this Application Control feature in a non-annoying way so you can get a better idea of why it’s popular.
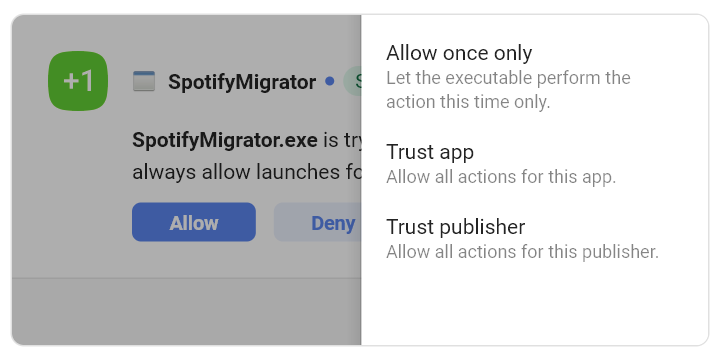
Basically, I’ll get a SpyShelter allow/deny alert when a new executable starts that isn’t with one of my trusted publishers. This is great to know from an informational perspective, because I can realize it when a new type of software I didn’t know was going to start is trying to launch.
In this example I just tried to launch Spotify which is automatically installed with Windows, which I do not normally use. You can see now that if this is a new software publisher I trust I can choose “Trust Publisher”.
Now, whenever that publisher launches an app it’s already trusted and I receive no allow/deny window for it. So, unless you are constantly installing new software 24/7, it’s pretty rare to get these alerts in my opinion. Besides maybe at first when you first start to use SpyShelter… it’s true at first you will get asked about a lot of publishers, and then that’s why you have to do some work to lock in your SpyShelter rules that let you control your trusted publishers.
For anti-code injection, I don’t believe I said you shouldn’t worry about it? If so, I apologize because you should worry about any security issues with your computer.
We made SpyShelter to monitor and worry about changes within the PC so we’re on your side for sure! I know I worry about changes to my PC all the time, so that’s why I am always looking at the SpyShelter “Events” tab. I hope there is some way with modern Windows to detect and block code injection, we are investigating it.
Thanks again and let me know if I misunderstood something!
I have opened a ticket for this, thanks for reporting this and sorry for the issue!
Yes, the old version worked that way, but as you have already explained, you can turn whitelisting off, which is cool.
But sorry for the confusion, I was just trying to make a point that ‘‘app behavior monitoring’’ is way more important to me than to block apps from running.
I have seen you mention that ‘‘SS can block malware from running’’ in several threads, but that’s why I mentioned that this is not interesting to me, since I will always disable the whitelisting feature anyway and my AV should take care of that. ![]()
So to clarify, SS only looks at if apps are in the ‘‘trusted publisher list’’ and if apps are signed or not? So it’s not actually scanning software for known malware signatures? I guess this is what I was confused about. I assumed you guys used a service like VirusTotal in order to decide if some app is safe or not. ![]()
Sorry for any confusion. These are two completely separate features.
The scanning is done by “Threat Protection”, which is the top item under “Protection” in SpyShelter. We don’t use VT, because they do not allow their APIs to be used that way legally. However, we make it easy to copy/paste our hashes so you can copy/paste hashes for any executable into VT manually if you want.
For our own Threat Protection feature we have created our own scanning system that uses multiple high quality rules/sources for checking executables, and we have had good feedback about it. But, if you don’t like that just switch it off.
The “Trusted Publisher List” is related to your own Application Control rules and is unrelated to “Threat Protection”. For example if you mark the publisher “Mozilla” as “Trusted” then everything from there is automatically allowed/installed with no allow/deny warnings from our side.
OK cool, but can you give a bit more info about this? So did you guys create your own AV engine, and what sources are you guys using? I mean how would this compare to any of the well known AV’s?
BTW, about the SS 15 GUI, is it resizable? Because currently it looks like it’s a huge vertical based GUI, it seems different compared to SS 12, see screenshots. I wonder how this would look like on a small 14 inch laptop screen, would you need to scroll to see the whole GUI? ![]()
We created a proprietary system that uses multiple threat sources and concepts. It should stand up to scrutiny against other AV engines.
Since it’s proprietary and we put a lot of time into it, we don’t share details. At first we only detected malware, but later we added PUP detection and so far we haven’t seen anyone report a false positive, or something we completely missed… but if that happens we would love to hear so we can keep improving the system.
Yes, you can make our UI smaller/larger and scroll around with it. I haven’t seen any reports of it being unusable, and we considered most common screen sizes.
Can you perhaps show me how it looks like when you resize the GUI? So will a scrollbar appear if you make the GUI smaller, so that it can fit on a smaller laptop screen?
OK I see, so in other words, SS is in fact offering a built-in AV. But is it cloud based or is it purely a locally based AV engine that gets updated once in a while?
BTW, you forgot to answer my question about Module 3, namely ‘‘Executable Insights’’, what does it exactly monitor, so what does it alert about?
It is cloud based 100%. We have nothing local on the PC.
Go to the SpyShelter “Activity” window ,then click an app icon. On the right side it will show “Insights” about the executable. Insights tells you a brief description of the app and what it does if we have information available. You can disable it if you don’t like it.
OK my bad, I thought it was supposed to alert you about stuff. I believe SS 15 does monitor webcam and microphone usage right? Which module covers this?
OK I see, so will it check the cloud everytime you open a .exe file or what?
And why did you guys decide to develop such a feature? Because like I said, most people will probably use Windows Defender, and it gets pretty good scores in most AV tests.
No, I think it only checks the first time SpyShelter runs.
Why did we develop such a feature?
Well, in our Activity list we found it frustrating to see the list of executables and if one had weird behavior we’d have to paste the hash to VT, so instead we made our own system (not VT) so we could easily glance and see if something was marked as “safe” by our own system, or not…
Also, we have two options where you can either allow PUPs and only stop Threats, or stop both. So, if for some reason you want to allow a PUP you can do so. Or, if you’re a security researcher just switch off this feature completely and then you can run whatever you want and watch its behavior in SpyShelter in “Events”.