And if it does, what type of code injection methods does it monitor, see link?
Thanks for asking this question!
If an .exe is injected into it can sometimes change its hash, and one of the main features SpyShelter has is hash monitoring. If you go to your SpyShelter Events tab and you see “binary changed” with a hash icon, that means an app’s binary has changed.
The second thing SpyShelter does is hold any unsigned executables. Injecting into an .exe can also make the executable unsigned in most cases from what I understand.
Therefore I think both of these features should help stop any injected executables.
However, some injection can be in memory and we may not be able to detect/stop that in our “easy” mode. But SpyShelter can prevent any new .exe from starting at all in our Paranoid mode, and in this case if that .exe was going to inject into another app it wouldn’t be able to start to do the injection in the first place.
If you are a security researcher and would like to try injecting into executables and let us know your results any feedback is appreciated! Be sure and run SpyShelter in Paranoid for your testing.
Yes, but I don’t know if hash monitoring is enough to detect code injection. And even if it did, it’s already too late to stop the damage. Like I said in the other topic, SS 15 should be focused on blocking malware post execution. So if some app manages to bypass AV, then SS should still be able to block it from doing damage.
In my view, SS should be able to block ‘‘process memory modification’’, the old SS Classic actually did have this option. So from what I understand, the new SS 15 doesn’t block code injection at all? For example, some malware use basic code injection, but others use more advanced ones like process hollowing. SS 15 should be able to block this, like any other decent behavior blocker. ![]()
Thanks for your feedback on improving SpyShelter with process memory modification. Our team will investigate if it’s possible to do something like that in the future.
You wrote “SS 15 should be focused on blocking malware post execution”. I don’t agree. Antiviruses focus on this and remediation, but our focus is on application control and allowing you to control what’s allowed to launch in the first place. Application control is something that antiviruses don’t usually do and that’s our focus, along with revealing what apps are doing in the background through visualization.
So in summary, we focus on letting you know what your apps are doing in the background, and app control. For example, maybe an app is not malware but it’s doing something you don’t like… with SpyShelter you can pick up on that activity and block it even though it’s not actually malware. Or maybe something is just annoying or wasting your resources… same thing… you can block it or prevent it from ever starting.
I get what you’re saying, but perhaps I didn’t explain it correctly, so I will give a bit more background info.
Basically I see SpyShelter as a tool that is meant to protect in case AV fails. So I completely agree with you that SS is about application control. If I’m correct, SS will alert about registry modification, service/driver installation and file/folder modification. This way you can control both semi-trusted apps and block malware from doing damage.
What I would rather disable is the whitelisting, I don’t want SS to alert me about every unknown app that I’m launching. That’s why always disable UAC, it’s too annoying. So basically if Win Defender (and VirusTotal) tell me a file is clean, I don’t want to be alerted about it. I do however want to be alerted about their behavior to get a clue if they might be malicious or not.
And that’s why I also came up with this idea to make SS alert about advanced code injection methods, because this is a widely used technique by malware.
Same goes for SS being able to alert about apps trying to capture the screen and clipboard, and webcam and microphone usage by apps. Not to forget about network access. And you should be able to configure SS in a way that it will automatically block certain stuff, without even alerting. This is all about app behavior control. ![]()
BTW, I just noticed in this blogpost that SS is apparantly able to block ‘‘Injections into other executables’’, so is this the same as blocking code injection?
Good catch! We planned to make the new version have a specific code injection protection feature but we did not implement it.
Instead, preventing an executable from launching (with our Paranoid or Suspicious modes) that could potentially inject into another application should prevent any injections.
I think we should probably update the article and change it so we don’t specifically mention that feature that was in the Classic version. Do you agree?
Yes, the article should obviously be changed if SS currently does not protect against code injection.
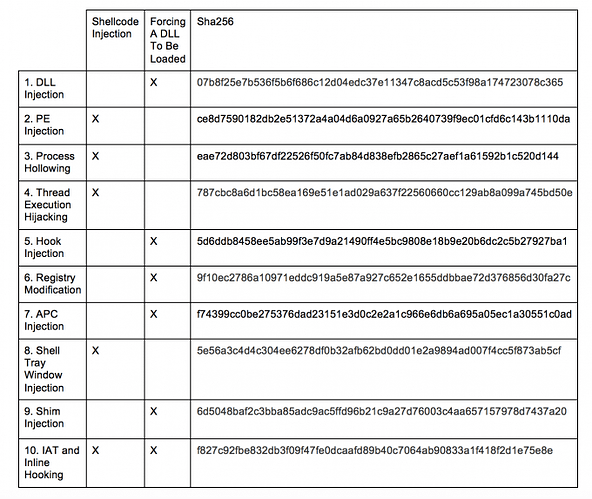
In my view, protection against code injection should be added though, it’s a dangerous and widely used technique that should be monitored by behavior blockers. Is this difficult to add in Win 11? From all the methods that were mentioned, I believe that at least the first 6 should be covered.
I have updated a ticket to update the web page. Thanks for pointing out that issue.
I have shared your comments with our team about looking at adding that functionality.
The text was removed from the page. Thanks again for letting us know of this issue.
BTW, perhaps it’s an idea to make it more clear on the SS website, what exactly each module does. I was looking at the SS screenshots on Softpedia and I noticed you’ve got 8 modules that you can enable/disable, namely:
1 Threat Protection
2 Application Security Control
3 Executable Insights
4 Registry Integrity Control
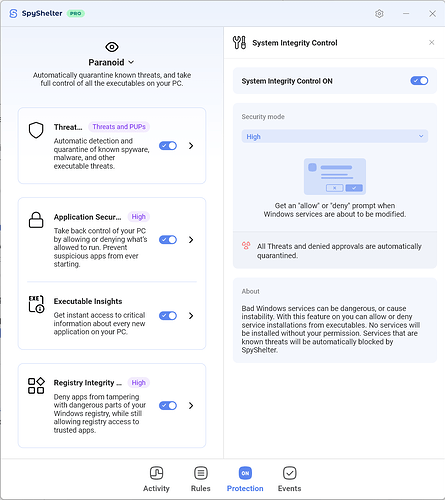
5 System Integrity Control
6 File Integrity Control
7 Screenshot Protection
8 Keyboard Protection (not yet developed)
Of course you guys do provide information, but a bit more info would be nice.
For example, I assume Module 1 is a cloud based AV and Module 2 is a whitelist. And it’s not clear to me what Module 3 exactly does. Which registry keys does Module 4 monitor?
Does Module 5 only monitor service/driver installation, or does it also monitor service/driver tampering? Some malware will try to disable certain service and drivers.
I assume Module 6 blocks access to certain folders (for example the Downloads and Documents folder), but can you also configure folders to be totally locked or read-only? And can you assign trusted apps that should be allowed folder access?
https://www.softpedia.com/get/Security/Security-Related/SpyShelter-Personal-Free.shtml
BTW, here is some more info about process/code injection.
Of course I don’t expect you guys to implement protection against all of this stuff, because it’s quite complex, but protection against basic code injection should be possible, similar to SS Classic. ![]()
I think that article may be our old out of date version. We no longer have the “Module 5” feature, but instead we prevent executables from launching at all so they can’t install drivers.
We do have the folder feature in our latest version under “File Integrity Control”. Yes, you can control the things above that you request. Please give it a try under “Protection”.
OK, so that’s what I meant, this means that the information should be updated. So basically, SS 15 doesn’t monitor code injection and service/driver installation, while SS Classic did.
But what I don’t understand is why didn’t you guys further develop SS 14, why did you guys decide to start from scratch? I assume that when you bought SpyShelter from Datpol (Polish company), you guys got all of the code right? ![]()
BTW, you didn’t answer my question about Module 3, what exactly does it alert about? And in which module are webcam and microphone access covered?
BTW, we already talked about this, but once again I have to mention that ‘‘preventing executables from launching’’ is basically an AV’s job, like Windows Defender. So to me that is no selling point, I wouldn’t buy SS for this. Or does SS 15 use a third party AV engine? Or is it based on VirusTotal? This is completely unclear to me.
That’s why I mentioned several times that the job of behavior blockers/anti-loggers like SS is to monitor app behavior. So apps that are already allowed to run (because AV says they are clean) should still be monitored for suspicious behavior, I suppose that’s what we call Zero Trust. And that’s why my goal is to get SS 15 at the same level as SS Classic in terms of protection, I think that should be the objective. ![]()
I see that protection against code injection is also mentioned in the ‘‘You Make The Rules With SpyShelter’’ section, this should also be corrected.
Use SpyShelter’s powerful “Rules” system to see how the executables on your PC are behaving, then block problematic behavior. For example, executables injecting into other executables, or unexpected changes to sensitive parts of the Windows Registry, and much more. You can even make rules based on publisher, for example you could allow all executable activity from Mozilla, or another publisher you trust.
Over here is mentioned that SS detects service/driver installation, this should also be corrected. But now that I think of it, shouldn’t the registry monitor (Module 4) in SS be able to block service/driver installation? ![]()
SpyShelter can allow or deny the following application behaviors with Windows:
- • Windows Registry Access (as mentioned previously)
- • New Windows Services
- • New Windows Drivers
- • Access to certain files and folders
Our software has System Integrity Control that should prevent services/drivers as you suggested. Sorry for any confusion. Please switch it on to try it out.
This is an interesting thing to post because it almost seems like you haven’t installed SpyShelter yet? Are you not using SpyShelter yet on your own PC?
We have a free trial where you can use all the features for a limited amount of time.
Perhaps you are a security researcher learning about different products? If so, that’s great and I’m glad to discuss SpyShelter with you and I enjoy doing so, but I think you’d have better understanding if you installed our app and turned on “Paranoid” mode under “Protection”. Then you can understand why people like SpyShelter.
SpyShelter lets you decide which apps/publishers are allowed to launch, so you can prevent privacy violating apps or adware apps from launching for example. We give you major control over your PC with our powerful “Rules” system.
We also keep track of software-related changes to your PC so you can see them in real-time. This may not be malware, but instead privacy violators, resource wasters, adware, and other badware type apps that aren’t specifically malware.
Please give SpyShelter a try if you haven’t? If I misunderstood something please let me know. And like I said, I really enjoy posting here in the forum and answering everything so please feel free to continue asking. If you use a Mac for example and you can’t use SpyShelter, I am glad to answer your questions, no problem!
It’s just surprising that you compare us to an AV because SpyShelter doesn’t look or act like one and it’s pretty obvious if you’re using it? Please install SpyShelter and give it a try.